Authored By: Threat Intelligence Team – CMC Telecom
TLP:CLEAR
I/ Executive Summary
Emerging in 2023, Dark Angels ransomware is a sophisticated threat believed to
have been derived from the leaked Babuk source code. It has since evolved into a
highly active and versatile ransomware strain, capable of targeting multiple platforms,
including Windows, Linux/ESXi environments. This adaptability makes it particularly
dangerous for enterprises with heterogeneous systems. Upon execution, the
ransomware begins by performing comprehensive system enumeration, gathering
information on processes, services, drives, and network resources. These enumeration
techniques allow it to disable critical services, terminate security-related processes,
and identify valuable targets for encryption. Leveraging multi-threading, it efficiently
handles the encryption process, ensuring maximum disruption in a minimal amount
of time.
The analyzed sample of Dark Angels ransomware demonstrates the use of advanced
encryption algorithms such as curve25519 for key exchange and HC-128 for
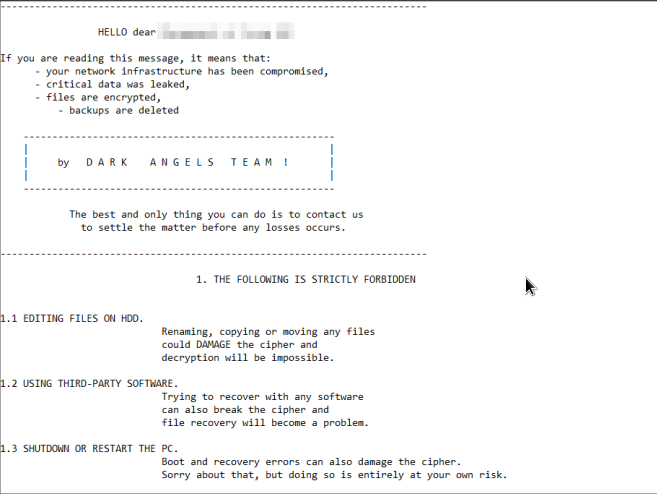
file encryption. During its operation, it creates a ransom note file named
How_To_Restore_Your_Files.txt, which provides victims with instructions for file
recovery, typically involving payment demands. All encrypted files are appended
with the .crypt extension, marking them as inaccessible. This combination of strong
encryption, multi-threaded execution, and multi-platform capabilities highlights Dark
Angels as a significant and evolving threat in the ransomware landscape, capable of
causing severe operational and financial damage to its targets.
II/ Detail
Filename: encr.exe
Filetype: PE32
Written Language: C/C++
MD5: b4a07cdd640bbaef21cd0493b4d62675
SHA1: 529e24c81ede5dfcedcc4fbc7d0030f985c67af1
SHA256: 38e05d599877bf18855ad4d178bcd76718cfad1505328d0444363d1f592b0838
First Seen/Detection Date: 2022-05-02
Initial Infection Vector: N/A
III/ Technical Analysis
This section contains technical analysis of Dark Angels sample provided in Scope
section.
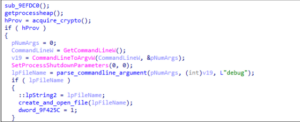
The Dark Angels malware begins by obtaining the process heap to manage memory
efficiently. It then sets up cryptographic operations necessary for its execution. If the
malware is executed with the “debug” command-line argument, it likely creates a log
file to record its operations or debugging information.
1. Service Enumeration
After that, the malware proceeds to enumerate system services, targeting specific
ones for disabling. These services are predominantly associated with backup solutions,
security software, and network monitoring tools. Upon detecting any of these services,
the malware terminates them by leveraging the CloseServiceHandle API.
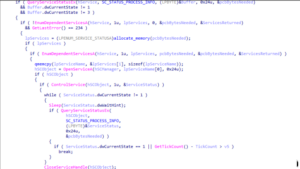
The terminated services are listed below.
• vss
• sql
• svc$
• memtas
• mepocs
• sophos
• veeam
• backup
• GxVss
• GxBlr
• GxFWD
• GxCVD
• GxCIMgr
• DefWatch
• ccEvtMgr
• ccSetMgr
• SavRoam
• RTVscan
• QBFCService
• QBIDPService
• Intuit.QuickBooks.FCS
• QBCFMonitorService
• YooBackup
• YooIT
• zhudongfangyu
• sophos
• stc_raw_agent
• VSNAPVSS
• VeeamTransportSvc
• VeeamDeploymentService
• VeeamNFSSvc
• PDVFSService
• BackupExecVSProvider
• BackupExecAgentAccelerator
• BackupExecAgentBrowser
• BackupExecDiveciMediaService
• BackupExecJobEngine
• BackupExecManagementService
• BackupExecRPCService
• AcrSch2Svc
• AcronisAgent
• CASAD2DWebSvc
• CAARCUpdateS
2. Process Enumeration
In addition to service enumeration, the malware conducts process enumeration by
invoking the CreateToolhelp32Snapshot API to capture a snapshot of all currently
running processes. It then iterates through these processes using the Process32First
and Process32Next APIs. If any of the process names match its predefined list, the
malware terminates them using the TerminateProcess API.
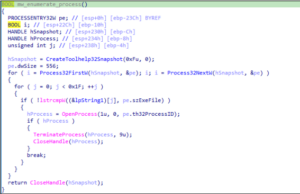
The terminated processes are listed below.
• sql.exe
• oracle.exe
• ocssd.exe
• dbsnmp.exe
• synctime.exe
• agntsvc.exe
• isqlplussvc.exe
• xfssvccon.exe
• mydesktopservice.exe
• ocautoupds.exe
• encsvc.exe
• firefox.exe
• tbirdconfig.exe
• mydesktopqos.exe
• ocomm.exe
• dbeng50.exe
• sqbcoreservice.exe
• excel.exe
• infopath.exe
• msaccess.exe
• mspub.exe
• onenote.exe
• outlook.exe
• powerpnt.exe
• steam.exe
• thebat.exe
• thunderbird.exe
• visio.exe
• winword.exe
• wordpad.exe
• notepad.exe
3. Delete Shadows
The malware first checks if it is running under WOW64. If detected, it disables file
system redirection using the Wow64DisableWow64FsRedirection API to gain direct
access to vssadmin.exe. It then executes a command via ShellExecuteW API to delete
all shadow copies silently. After completing this operation, the malware re-enables
file system redirection using the Wow64RevertWow64FsRedirection API, restoring
normal system behavior.
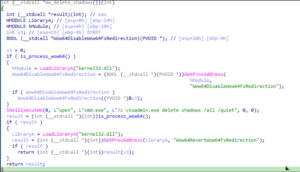
4. Network Enumeration
The malware supports “shares” and “paths” as command-line arguments. When
these arguments are provided, the malware uses them to enumerate network shares,
potentially identifying accessible resources. This behavior suggests the possibility of
lateral movement, as the malware may leverage these identified shares to propagate
across the network or access additional systems.
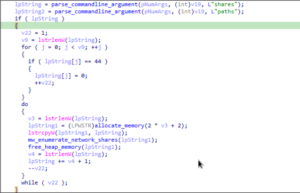
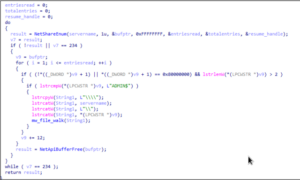
The malware uses the NetShareEnum API to enumerate shared network resources.
This process lists all accessible network shares while specifically excluding certain
administrative shares.
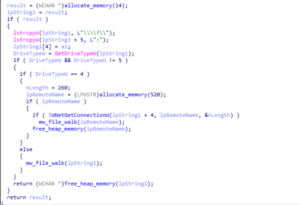
The malware processes drives by constructing their paths and identifying their types
with the GetDriveTypeW API. For network drives, it retrieves the corresponding remote
network path using the WNetGetConnectionW API and proceeds to enumerate files
on the network share.
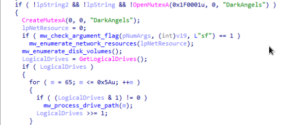
The malware creates a mutex named “DarkAngels” to prevent multiple instances
of itself from running simultaneously on the system. When executed with the “sf”
command-line argument, it enumerates network resources, scanning for accessible
shares or network paths to target.
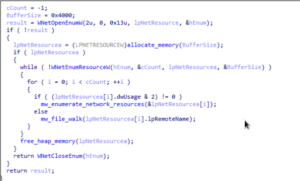
The malware employs the WNetOpenEnumW API to begin enumerating network
resources, either starting from a specific resource or the network root. It then
repeatedly calls the WNetEnumResourceW API in a loop to retrieve and process
batches of network resources individually.
IV/ YARA Rule
rule MAL_Ransomware_DarkAngels_Win_x32_Nov15 {
meta :
author = "@cmccybersec"
source = "cmctelecom.vn"
date = "30.11.2024"
strings :
$hex1 = {83 7 D F8 00 0 F 85 ?? ?? ?? ?? 83 7 D F4 00 0 F 85 ?? ?? ?? ??
68 4? 3 C ?? ?? 6 A 00 68 01 00 1 F 00 FF 15 ?? ?? ?? ?? 85 C0 75 11 }
$hex2 = { E8 12 52 00 00 E8 AD 81 00 00 E8 A8 9 E FF FF A3 60 42 ?? ??}
$hex3 = {68 18 3 C ?? ?? 8 B 4 D C8 51 8 B 55 E8 52 E8 FF 9 F FF FF 83 C4
0 C 89 45 BC 83 7 D BC 00 74 27}
$str1 = "DarkAngels"
condition :
all of them
}
V/ IOCs
Other Sample Hashes
c673ff72d038ff5caa1c1088bfe6c36f7f9f4c58b9b03e28e73446be33c82cb0
7533 fb19ab297a90dfdcb3809a89e835ee70d1244cee6ddd31a53b5941751bd4
VI/ MiTRE ATT&CK
1. TA002 Execution
(a) T1059 Command and Scripting Interpreter
i. T1059.003 Windows Command Shell
(b) T1106 Native API
(c) T1106 Native API
(d) T1129 Shared Modules
2. TA003 Persistence
(a) T1543 Create or Modify System Process
i. T1543.003 Windows Service
3. TA005 Defense Evasion
(a) T1027 Obfuscated Files or Information
4. TA005 Discovery
(a) T1007 System Service Discovery
(b) T1135 Network Share Discovery
(c) T1057 Process Discovery
(d) T1082 System Information Discovery
(e) T1083 File and Directory Discovery
(f) T1518 Software Discovery
5. TA0034 Impact
(a) T1486 Data Encrypted for Impact
(b) T1489 Service Stop
(c) T1490 Inhibit System Recovery